Foldr can operate as a SAML single sign-on Identity Provider (IdP) or Service Provider (SP)
When Foldr is configured as a Service Provider, it allows users to sign into Foldr using a third-party authentication service. In this scenario, a user is redirected to another IdP such as Active Directory Federation Services or Microsoft Azure SSO to sign in before being directed back to the Foldr app to access their files.
Security Considerations – Prompting for LDAP Passwords vs Using Service Accounts (SMB Share Access)
Active Directory and traditional on-premise Windows SMB file servers have no concept of SAML or SSO access tokens. As such, when users are signing into the Foldr appliance without directly providing their password to the system, it is not possible for Foldr to provide the usual granular ACL / security permission access to the shares for that user.
The administrator has two different options to this issue:
1. Prompt users for their LDAP password (Recommended)
The first time a new user signs into Foldr using SSO, they will receive a prompt to provide their LDAP / Active Directory password.
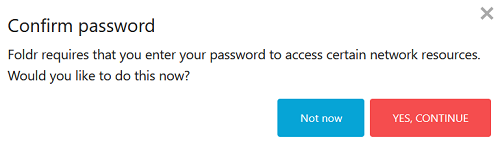
The password is a required to access SMB shares as the user that is signed in and the Confirm Password prompt is a one-time operation, provided the user supplies the password. If the user clicks ‘Not now’ or fails to provide the correct password, they will be prompted again the next time the user signs in. Until the correct password is provided, SMB shares will be missing from the My Files interface.
Once the user has provided the correct on-premise AD password for SMB access, they will not be prompted again in future login sessions, until their domain password is changed outside of Foldr. It is optional, but recommended to allow users to change their Active Directory passwords inside Foldr by enabling LDAPS and password change on the Foldr server.
Once the Foldr appliance has the users password, it is encrypted and stored within the configuration database and can then be used for future sessions. A benefit of this approach is that service accounts are not required for access to SMB shares and Foldr can operate in the normal manner of respecting all existing security ACLs on the file servers providing access to the shares / data. You can enable the prompt for network credentials feature when enabling the SSO service within Foldr Settings > Single Sign-On > Service Provider.
2. Use fixed service accounts on each SMB share to present shares to users
Instead of prompting users for their LDAP / on-premise Active Directory password, the Foldr admin can use a suitable service account to present SMB shares to users. Service Accounts are configured within Foldr Settings > Integrations > Service Accounts and should be configured using the domain UPN (username@domain.internal) as its username. The service account must have permissions to access the file server shares being presented with appropriate permissions and these accounts are then applied to each SMB share in turn wihtin Foldr Settings > Files & Storage > Edit-Share > Access tab, also ensuring that the ‘Use service account for all access‘ toggle is also enabled.
Permissions and Service Accounts
This approach, by default, (using service accounts and the ‘use service account for all access’ switch) will not allow Foldr to respect the users’ own security permissions/ACLs on the backend storage and instead users will receive permissions that apply to the service account user. The administrator can still control read or write access to each share for the service account using the share permissions in Foldr Settings > Files & Storage.
Granular user permissions/ACL support when using Service Accounts
The Foldr server is able to parse the backend file server permissions (Windows SMB file server shares only) with the optional toggle ‘Enable full ACL support (when using a service account for access)‘ within the Files & Storage > Access tab.
Setup Process
1. Ensure Foldr is publicly accessible and that a signed SSL certificate is installed on the appliance.
2. Sign into the Azure portal using your administrative credentials and browse to Azure Active Directory >> Enterprise Applications >> + New application
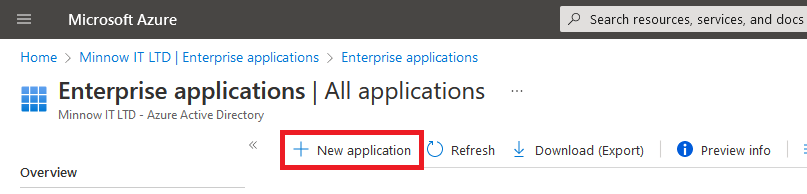
3. Click + Create your own Application
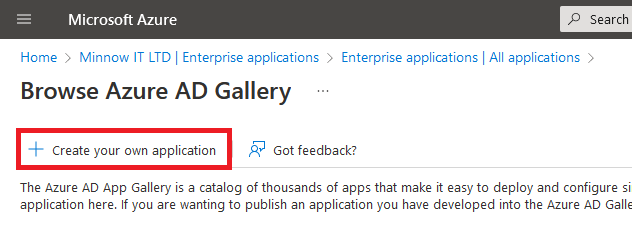
4. Give the application a suitable name, leaving the option to ‘Integrate any other applicaiton you don’t find in the gallery..’ selected and click Create. It will take a few moments to process and add the application.
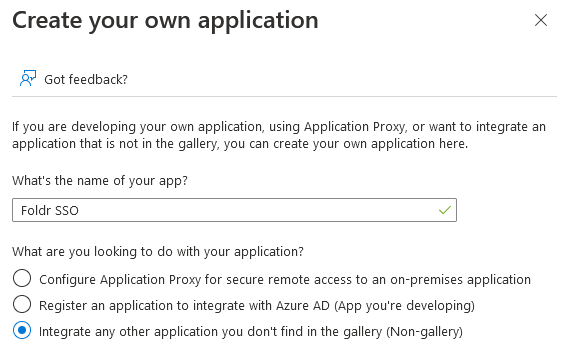
5. The view will update with the app summary page. Click Single sign-on
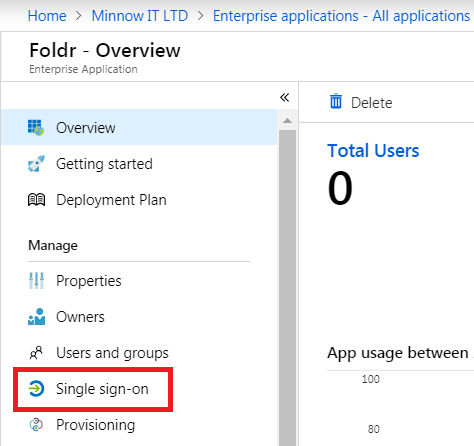
6. Select SAML from the options available

7. Click the Edit button in section 1 labelled ‘Basic SAML Configuration’
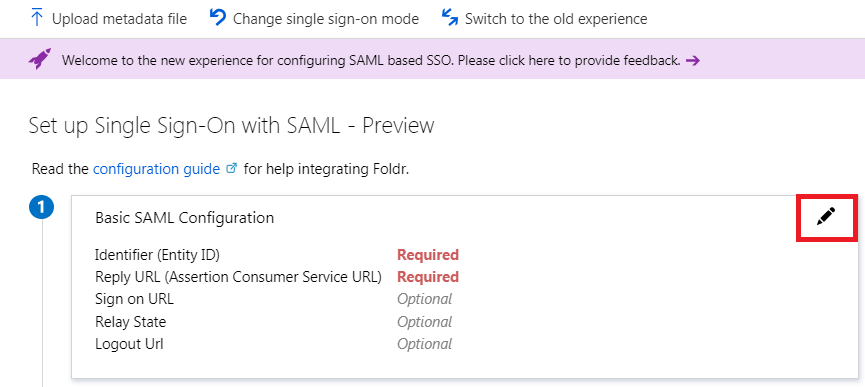
8. Configure the Identifier (Entity ID) and Reply URL (Assertion Consumer Service URL) fields as follows:
Identifier (Entity ID) = https://public-address-of-foldr/sso/sp
Reply URL (Assertaion Consumer Service URL) = https://public-address-of-foldr/sso/sp/acs
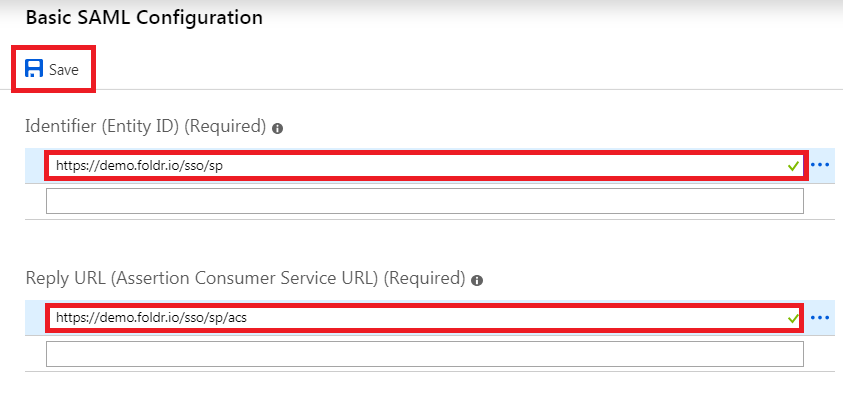
Click Save and then click the X (top right) to close the dialog
9. Scroll down to section 3 labelled ‘SAML Signing Certificate’ and click the download link to download the Azure SAML signing certificate in Base64 format. Save the certificate to your desktop as it will be used later in the setup process.
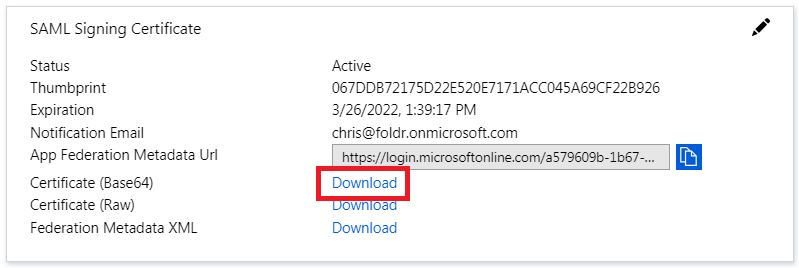
NOTE – It is important to make a note of the Expiration date shown in this dialog and set a reminder to renew this certificate before it expires. If this certificate expires, it will impact users trying to sign in via Foldr and SSO. See the Troubleshooting section at the bottom of this article for the steps required to generate a new signing certificate.
10. Log into Foldr Settings and browse to Single Sign-On > Service Provider
Enable the switch labelled Enable SSO with external Identity Provider?
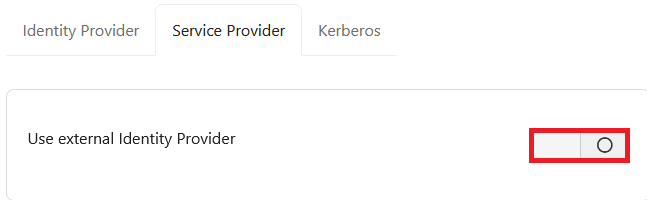
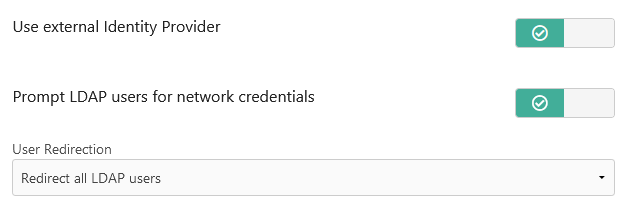
11. Decide on the following and enable the switches as appropriate:
– Whether new/unknown users to the Foldr appliance should be prompted (once) to provide their password to be stored in the appliance vault – or if service accounts are to be used to present SMB storage.
– Whether Foldr should automatically redirect LDAP users to Azure to authenticate. This is recommended unless local Foldr accounts are also being used without SSO. There is also a granular option under the User Redirection drop-down menu if only specific users or groups should redirect to Azure to sign in.
In most scenarios (prompting users for password instead of using service accounts) the following options are enabled.
12. Go back to the Azure portal and scroll down to section 4 labelled ‘Set up <app-name>’
Copy the following three fields and place them into the corresponding fields in Foldr Settings >> Single Sign-On >> Service Provider
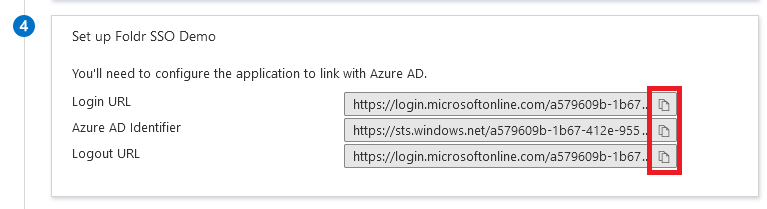
Login URL >> Sign-In Url
Azure AD Identifier >> Issuer
Logout URL >> Sign-Out Url

13. Using a text editor, open the Azure SAML signing certificate that was downloaded at step 9 and paste into the ‘Validation certificate’ field in Foldr Settings >> Single Sign-On >> Service Provider
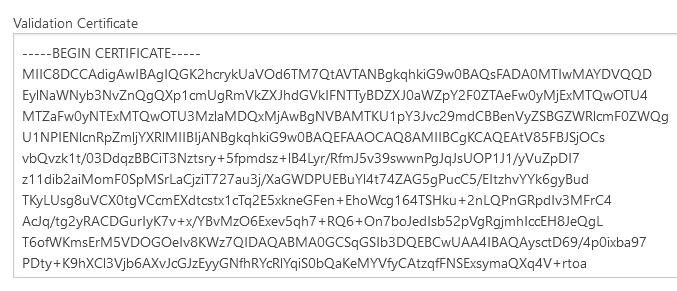
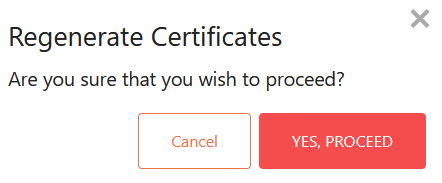
14. Scroll down the page and click Regenerate
![]()
Click Yes, Proceed on the prompt to populate the Certificate and Key fields
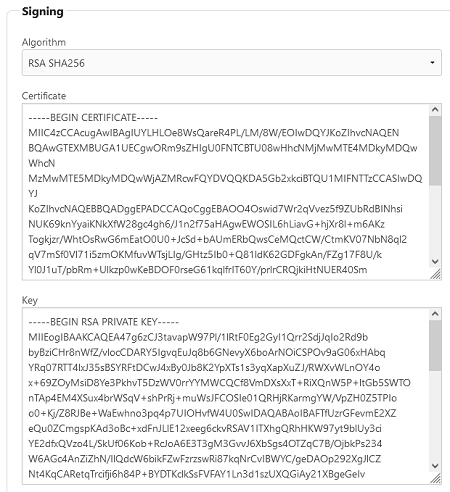
Click SAVE at the top of the page.
15. Go back to the Azure administration portal and select Users & Groups inside the Enterprise app
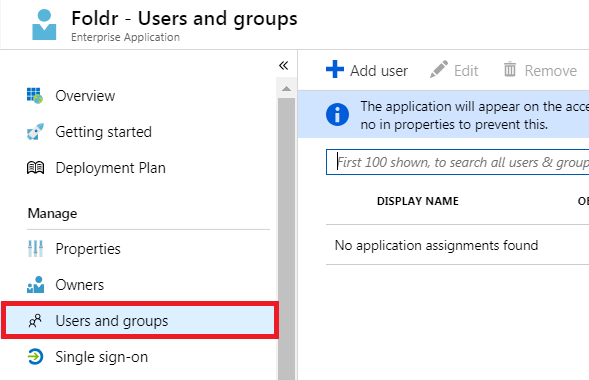
16. Browse and select the users that you wish to use the SSO integration. Finally click SELECT to confirm.
The SSO integration is now complete. A user browsing to the Foldr URL should be automatically redirected to Microsoft’s sign-in page after providing their username. After signing into Microsoft Online / Office 365 the user should be automatically redirected to Foldr and presented with their storage locations in the interface. If the user is new / unknown to the Foldr server, they will be prompted to provide their Active Directory password – if that option has been enabled and SMB shares are being presented.
Note – Unlike AD FS based SSO, there is currently no support for SAML sign-out, so users will need to ensure they sign out from Microsoft Office 365 first and then Foldr, to be fully signed out of the Foldr app.
App Compatibility
Signing into Microsoft Online / Azure using SSO is supported in all Foldr apps – web, mobile and desktop providing the ‘Use web sign-in‘ feature is enabled for each app type on the server within Foldr Settings >> Devices & Clients. Note that web sign-in is ON by default for all app types.
Foldr for Windows – sign in with Azure SSO:
Foldr for macOS – sign in with Azure SSO:
Troubleshooting
Error (401) Signature Validation Failed
It is important to note the expiry date of the SAML Signing Certificate shown in the Azure portal displayed in the app registration being used by Foldr (step 9 above). Should this certificate be allowed to expire, the following error will be shown in Foldr when a user tries to sign in with SSO.
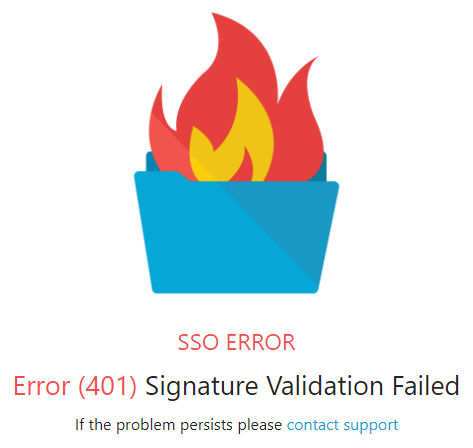
The Foldr / Azure admin, should manage the SAML signing certificate by creating a new certificate before expiry date, mark it ‘Active’ and then download and paste it into Foldr Settings, replacing the existing Validation Certifciate shown in Foldr Settings > Single Sign On > Service Provider. The steps given by Microsoft to handle this process are as follows:
1. In the Azure portal, go to Enterprise App Registrations, edit the app and select the Single sign-on > SAML.
2. In section 3, the SAML Signing Certificate section, click Create new certificate.
3. Choose a duration of up to 3 years, then click Save, then click OK.
4. Select ‘Make new certificate Active’ and click Save at the top. This will roll over your existing certificate to the newly created certificate.
5. Download the new certificate in BASE64 format, and upload it to Foldr Settings > Single Sign On > Service Provider.
6. Click Save Changes